How to Secure a Website with 8 Essential Steps (2024)

Website Malware Scan
Enter a URL to check for malware, viruses, blacklisting status, website errors, malicious code & more.
As a website owner, securing your website is of utmost importance. Cyber threats, such as hacking attempts and malware infections, can not only compromise your website’s functionality but also put your visitors at risk. In this article, we will delve into the details of securing a website, equipping you with essential tools and techniques to maintain a safe online presence.
Table of contents
How to check a website for malware
Securing a website begins with conducting a thorough check for malware. This initial step is crucial in identifying and addressing any potential threats that could compromise your website’s integrity and the safety of its visitors. Consider the following practical approaches for checking your website for malware:
Method 1: Use a website malware scanner
Online website scanning services like Sucuri SiteCheck and Google Safe Browsing are reputable and powerful tools that can thoroughly evaluate your website for possible malware infections. Simply visit their websites and enter your website’s URL to initiate the scanning process.
For example, here’s how you can scan your website for malware with Sucuri SiteCheck:
- Go to the Sucuri SiteCheck page.
- Enter the URL of your website (example.com), then click Scan Website.
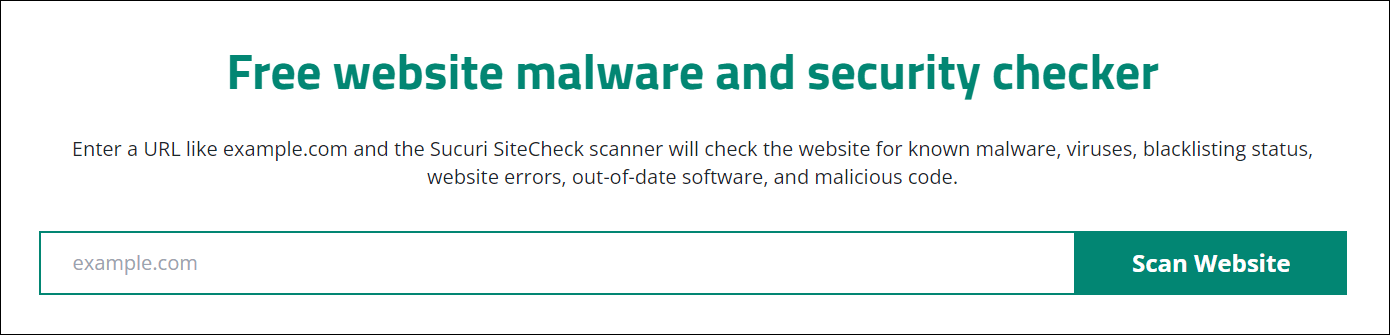
- Sucuri will initiate the scanning process, and within seconds, it will provide you with the results. The report will include any identified malware on your site, whether your site is blacklisted, and an assessment of your site’s overall security level.
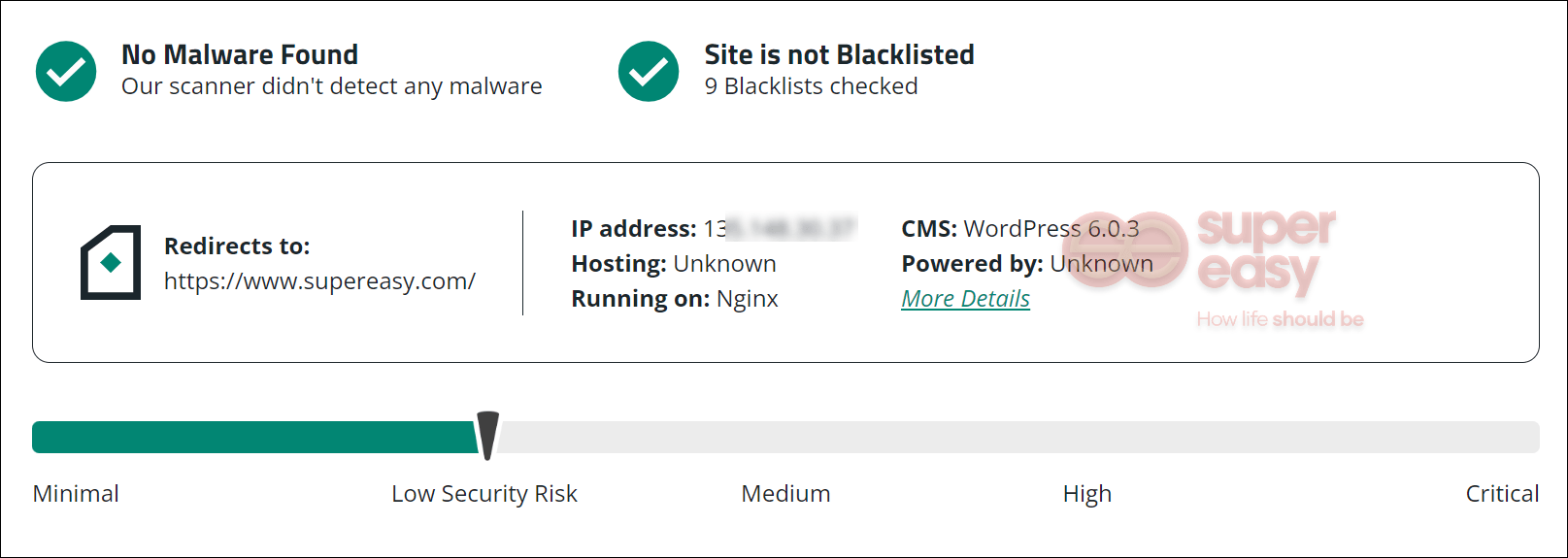
If your website has been infected with malware, it’s crucial to take immediate action to remove it and restore the security of your website. Remember, website malware removal can be a complex process, and it’s advisable to seek professional assistance if you’re unsure or unable to handle it yourself.
>> How to remove website malware & viruses
Method 2: Check Blacklisting Status
Websites infected with malware are often blacklisted by search engines and security companies. So checking the blacklisting status of your website is another way to check your website for malware. You can simply use dedicated tools like Sucuri SiteCheck or VirusTotal.
Alternatively, if your website is registered with Google Search Console, you can access the Security issues section to check if Google has flagged your website for any security-related issues or blacklisting.
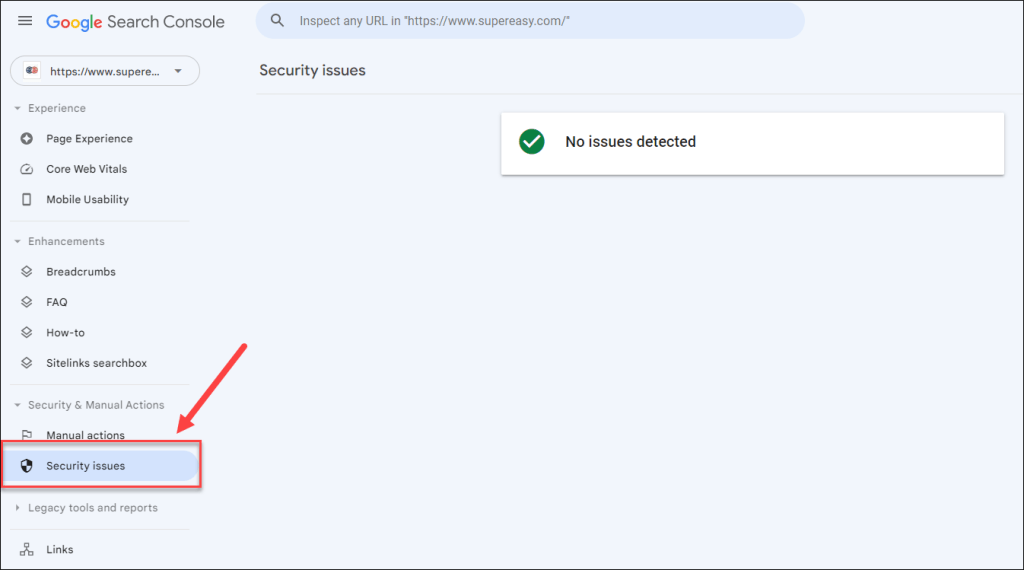
If your website is blacklisted, it’s important to take immediate action to rectify the situation and request removal from the blacklist.
>> How to remove your website from blocklists
Method 3: Perform thorough review of website behavior and source code (manually)
Check your website’s behavior and content for any signs of malware. Look out for excessive pop-up ads, frequent redirects to unrelated websites, unusual website performance, or unexpected changes in your website’s appearance.
You can also analyze the site code. It’s important to pay attention to script attributes and hidden iframes. Take note of lines that start with “<script src=>” or “<iframe src=>” and carefully analyze the URLs or file names that come after them. If you are unfamiliar with these URLs or file names, it could indicate the presence of malicious scripts.
8 essential steps to secure a website
In this section, we will explore seven essential steps to secure a website effectively. By following these key measures, you can establish a strong security foundation and minimize the risk of data breaches, unauthorized access, and other cyber threats.
1. Keep software up to date
Outdated software often contains vulnerabilities that malware can exploit, so prompt updates are crucial. Regularly update your website’s software components, including the content management system (CMS), plugins, themes, and scripts. Enable automatic updates whenever possible to ensure prompt installation of the latest security fixes.
2. Implement strong user authentication
Weak passwords are easy targets for attackers seeking unauthorized access. So make sure that all user accounts associated with your website have strong and unique passwords. Consider using a password manager to generate and securely store complex and unique passwords. It’s also recommended to implement multi-factor authentication (MFA) or two-factor authentication (2FA) to add an extra layer of security.
3. Employ Web Application Firewalls (WAF)
Implementing a Web Application Firewall (WAF) is crucial for securing a website. A WAF acts as a protective barrier between your website and potential threat: It filters out malicious requests and suspicious activities, protects against common threats like SQL injections and XSS attacks, and detects zero-day attacks[1] and advanced malware. It mitigates vulnerabilities with virtual patching[2] and allows granular access controls based on various factors[3]. Additionally, it provides real-time monitoring, detailed logs, and comprehensive reports for effective threat management.
It’s important to choose a reliable WAF solution to fortify your website. When it comes to trusted options, Sucuri Inc. stands out as a globally recognized authority in website security. Their Website Firewall, in particular, is highly regarded for its effectiveness in securing websites.

- Cloud-Based Website Firewall (actively blocking malicious traffic)
- Stop Hacks (Virtual Patching/Hardening)
- Advanced DDoS Mitigation
- Intrusion Prevention System
- HTTPS & PCI compliant (SSL automatically enabled)
- CDN Speed Enhancement (reducing server load by 80%)
- High Availability/Load Balancing
Note that Sucuri’s Website Application Firewall goes beyond enhancing website security; it also helps preserve your website traffic and rankings and increase your website performance. For example, by leveraging a global Content Delivery Network (CDN), Sucuri’s WAF optimizes content delivery, reducing load times for visitors across different locations.
4. Enable HTTPS
To establish a secure line of communication between your website and its visitors, it is imperative to implement an SSL/TLS certificate. This certificate allows theuse of the HTTPS protocol, replacing the less secure HTTP. By doing so, you create an encrypted connection that effectively protects sensitive data transmitted between your website and its users.
Enabling HTTPS has multiple benifits. When visitors see the padlock icon and the “https://” prefix in the website URL, they know that they are interacting with a legitimate and safe website and not a fraudulent or malicious one. Additionally, HTTPS has been a ranking signal in Google’s search algorithms since 2014, meaning that websites using HTTPS may have a slight advantage in search engine rankings.

The good news is that securing your website with an SSL/TLS certificate does not require any technical expertise. Many hosting companies offer SSL/TLS certificates as part of their hosting packages, often at no additional cost. If your hosting provider does not, you can obtain one for free from reputable Certificate Authorities (CAs) like Let’s Encrypt.
Step-by-step guide: How to get a free certificate for your website’s domain from Let’s Encrypt
5. Practice secure file uploads

To ensure a secure environment for file uploads, it’s important to implement reliable mechanisms that prevent the upload of malicious files. Validate and sanitize user input effectively to mitigate potential code execution vulnerabilities. It is also recommended to store uploaded files outside the web root directory or apply stringent access controls to restrict unauthorized access.
6. Secure error messages
Error messages play a crucial role in troubleshooting website issues, but they should not reveal sensitive information that could be exploited by attackers. For example, instead of specific messages, consider generic ones that inform users about errors without exposing system or application vulnerabilities.
7. Perform regular backups
Regularly back up your website’s data to an external location. In the event of a malware infection or other security incident, backups provide a reliable way to restore your website to a clean state. Ensure that backups are performed consistently and verify their integrity periodically.
There are various backup solutions available, including plugins, server-level backup tools, or cloud-based backup services. Make sure to select one that suits your website’s platform and hosting environment, and consider factors such as ease of use, automation capabilities, storage space, and restoration options when choosing a backup solution.
8. Educate Yourself and Your Team
Train yourself and your staff about common attack vectors, social engineering techniques, and safe browsing habits. Encourage strong security practices, such as regular password updates and cautious handling of sensitive information.

6 most common website security threats
In the ever-evolving digital world, modern websites face a range of security risks that can jeopardize their integrity and compromise sensitive data. In this section, we will delve into the prevailing vulnerabilities and threats that website owners must be vigilant about.
Cross-Site Scripting (XSS)
Attackers inject malicious scripts into web pages, allowing them to execute unauthorized actions or steal sensitive data from users.
SQL Injection
By inserting malicious code into the website’s input fields, hackers manipulate the SQL queries sent to the database, potentially gaining unauthorized access, extracting sensitive data, or performing unauthorized actions.
Distributed Denial of Service (DDoS) Attacks
DDoS attacks occur when malicious actors overwhelm a website with a massive influx of traffic, causing it to become unavailable to legitimate users. DDoS attacks are a form of non-intrusive internet attack that pose a significant threat to website owners and are an essential aspect of the security landscape. These attacks exploit vulnerabilities in resource-intensive endpoints, making even a small amount of traffic sufficient to cause significant disruption and compromise the targeted website.

Malware Infections and attacks
Websites can become infected with malware, which can harm visitors, compromise sensitive data, or perform malicious actions on the website itself.
Brute Force Attacks
Hackers attempt to gain unauthorized access to a website by systematically trying numerous username and password combinations.
File Inclusion Vulnerabilities
Attackers exploit insecure file inclusion mechanisms to execute malicious code on a website, potentially leading to remote code execution.

That’s pretty much all we have to share on how to secure a website. Hope you find the post helpful. If you have any questions or suggestions, feel free to leave a comment below.
[1] A zero-day attack refers to a cybersecurity incident that exploits a vulnerability or security flaw in software that is unknown to the software vendor or has not yet been patched. This means that cyber attackers can exploit the vulnerability before a fix or patch is available, leaving organizations vulnerable to targeted attacks.
[2] Virtual patching refers to a security measure that aims to mitigate vulnerabilities in software applications without modifying the actual application’s source code or waiting for an official patch from the software vendor. It provides a temporary solution to mitigate the vulnerability until a permanent fix is developed and implemented.
[3] Granular access control and customization options allow you to configure rules, exceptions, and whitelists/blacklists tailored to your website’s functionalities while maintaining security. You can have precise control over access based on factors like IP addresses, user agents, geolocation, and specific URL patterns. This way, legitimate traffic is not unnecessarily blocked while potential threats are still effectively mitigated.
Credit: Featured image from sucuri.net

 View all of Jocelyn Sun's posts.
View all of Jocelyn Sun's posts.