How to Find out Who Hacked My Email – 2024 Guide

Nowadays, your email account has become a prime target for hackers. If you detect fraudulent attempts to access your account, you might be wondering who did that! In this guide, you should find some valuable information.
Is it possible to find out who hacked my email
The answer is, it depends. And you can check which IP they used to access your account. Usually, email service providers keep a record of your account’s recent activities, with which you can drill down further to see the IP addresses.
How to check your email login history
To identify the IP address of your account logins, all you have to do is take the steps as follows.
Gmail
1. Open your Gmail inbox.
2. Click Details next to the Last account activity line at the bottom of the page.
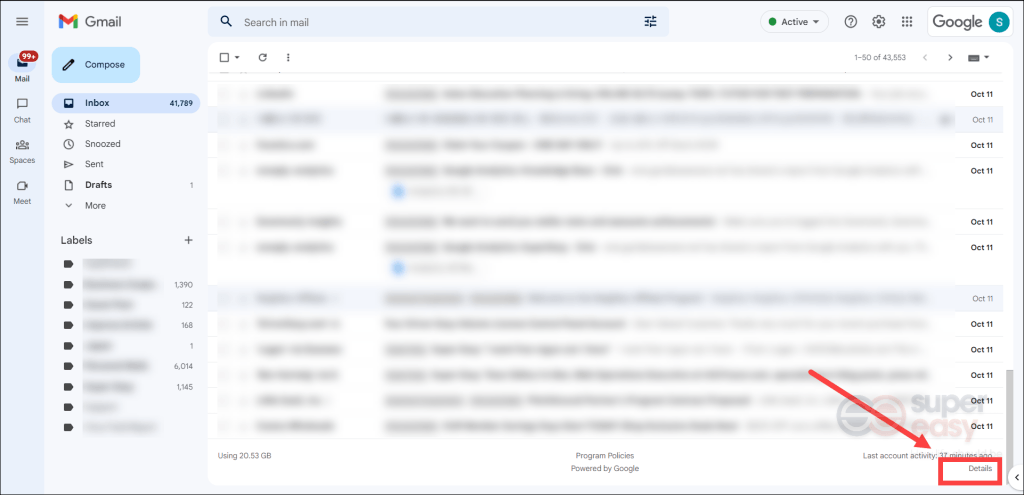
3. On the page of your account’s recent activity, you’ll see the column Location (IP address) showing you the list of IP addresses of recent logins in your account. If there are any logins that didn’t belong to yours, copy that IP address and perform an IP address lookup.
Outlook
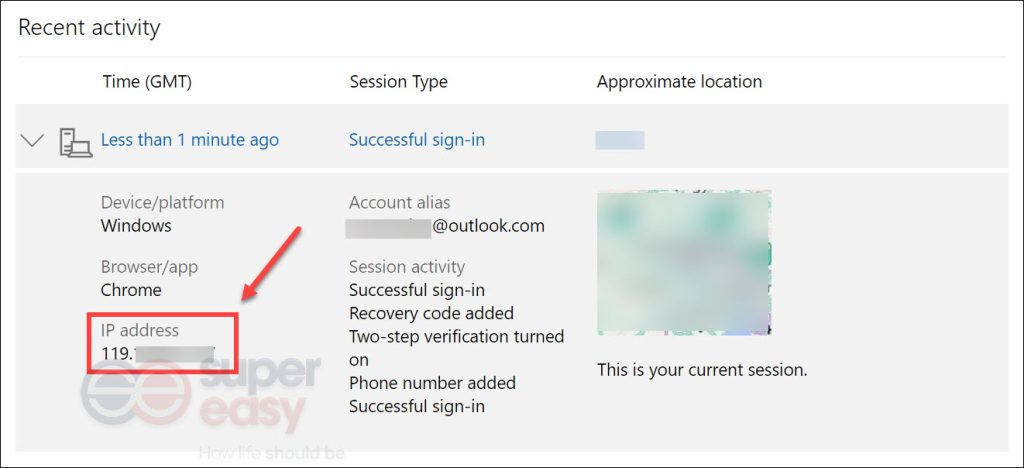
1. Navigate to the Recent activity page and sign into your account.
2. Now you should be able to see when and where you’ve used your account within the last 30 days.
3. In the Recent activity section, look for the login attempt that was fraudulent. Click on it and copy the IP address. Then perform an IP address lookup below to dig out more details.
How to conduct an IP address lookup
To get IP details, simply go to the NordVPN IP Address Lookup page. Then paste that unidentified IP address you just copied into the search box and click Get IP Details.
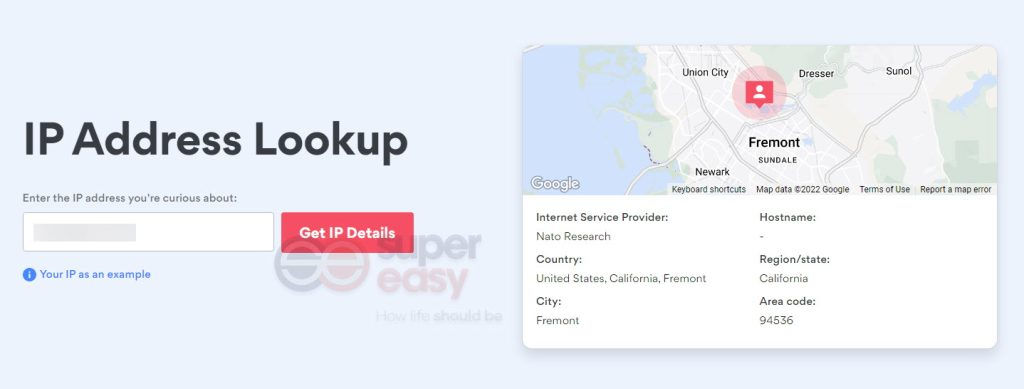
Even though you can conduct an IP address lookup, all you can find out is the city, state, zip code and country of that IP address, which may not seem valuable for you. So it’s very unlikely that you will track down the person behind it. Besides, there’s a high chance that it was an automated hacking program that attempted to gain access to your account, making it impractical to track them down.
However, if you manage to find some clues, be it a username, phone number, or mailing address that’s included in an email that was sent by the hacker, you can conduct a reverse lookup with Spokeo. Spokeo is a people search service with years of experience in providing users with access to billions of public records. You can use a name, phone number, email address, or even an online username as the search query to search for the following information that’s included in an easy-to-read report:
Contact info
Names, aliases, phone numbers, and email addresses.Personal details
Birth information, marital status, education level, hobbies + interests.Location history
Current address, past addresses, residents, neighbors, etc.Family & Associates
Family members, household demographics, birth records, and marriage records.Court records
Criminal records, DUIs, sex offenses, and more!Social media accounts
Social media, usernames, dating sites, music & gaming accounts.
How to prevent future hacks
A hacked or compromised account can put you at risk for identity theft. In addition, your friends and family may fall victim to spoofing emails if a fraudster gets the hold of your login credentials. Therefore, it’s imperative you know how you can prevent it from happening again.
Before learning how to prevent future hacks, you should have some basic knowledge about how your email account fell into the wrong hands. Generally, you fall victim to email hacking because:
- You’re using a weak or easy-to-guess password.
- You were tricked into clicking on a link or opening an attachment that contains viruses and other malware.
- Your personal information has been exposed in a data breach.
- You were using a public Wi-Fi that isn’t secure.
4 tips to protect against an email hack
Now you can take precautionary measures as follows.
1. Create a stronger password
Whenever you discover that your email has been hacked, the first thing you should do is to change your password. There are some golden rules for creating a hacker-resistant password.
- Use a combination of lowercase letters, uppercase letters, numbers, and special characters.
- Avoid creating a password that contains your personal information, eg. your name and birthday.
- Don’t use the same password as the one you do on other accounts.
If this sounds like a daunting task for you, consider using a password manager like LastPass to help you create a strong password and manage all login credentials for you. It has strong encryption algorithms, local-only encryption and multifactor authentication to add extra layers of security. Thus you can rest assured that you use LastPass to generate and manage your passwords.

PASSWORD GENERATOR TOOL
Generate long, randomized passwords that protect against hacking instantly.
2. Enable 2-step verification
2-step verification is a security feature that helps protect your accounts and your passwords. If you set up 2-step authentication, you’ll need to enter a one-time code delivered by text to your phone or other device in addition to the account number and password. That’s essential to maintain a strong security posture as it neutralizes the risks associated with compromised passwords. Intruders without access to your security info cannot log in, even though they have your password.
Below is how you can enable 2-step verification on your Google and Microsoft account.
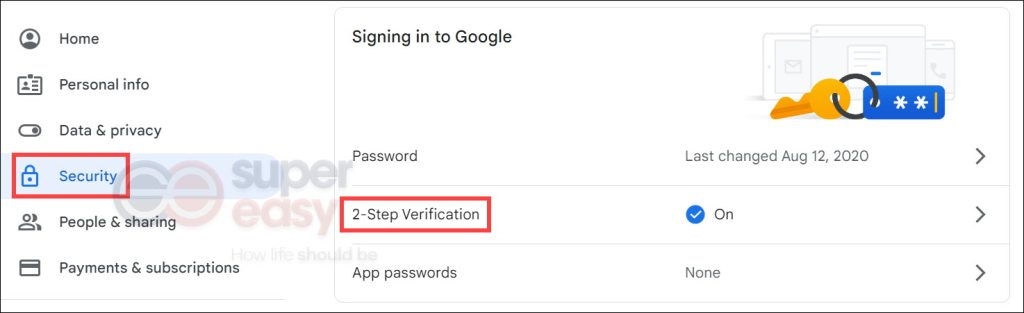
1) Open your Google Account.
2) In the navigation panel, select Security. Find 2-Step Verification, click on it and then follow the on-screen instructions to turn it on.
Microsoft
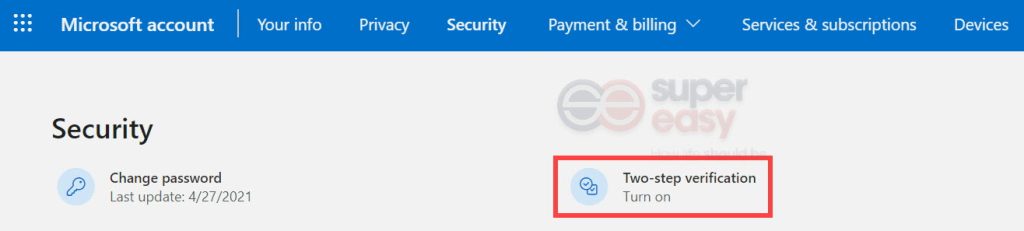
1) Go to the Security basics page and sign into your account.
2) You’ll see Two-step verification. Click on it and follow the on-screen instructions to turn it on.
3. Use a trustworthy antivirus on your devices
While there is no one silver bullet to avoid getting a virus on your devices, installing antivirus software is still an effective way to protect your devices and mitigate the risk of your information being stolen.
If you have no idea which antivirus software to choose, you can give Norton a shot. It provides you with powerful protection against viruses, malware and other online threats.

Award-Winning Antivirus Software
4. Regularly check if your personal data has been exposed
One of the most common causes for a hacked email is that your passwords associated with your email address have been exposed in data breaches or on the Dark Web. Sometimes you’re not to blame. To minimize your losses, we suggest you run a free scan on Aura and check if your personal data has been exposed. All you need is to enter the email address and you’ll get a report of known exposed information and recommendations for protection.
Living in this digital world, our life has become easier and more convenient. However, our identity is being put at risk due to compromised personal information. Therefore, we should do our due diligence to prevent our own identity from being stolen. One of the most effective way to keep us safe is to use and Identity Theft Protection and Monitoring Service like Aura, which is rated as #1 on Security.org. Whenever they detect any threats to your identity, accounts, and more, they will alert you. In addition, Aura can help reduce spam and robocalls by requesting the data brokers who collect and sell your info to advertisers and telemarketers to remove your data.
Identity Theft Protection
Get alerted if your registered Social Security Number (SSN), online accounts, and other personal information have been compromised online.
Final words
Email is one of standard ways of sending and receiving information in today’s world. Besides, we sometimes use our email to log into other accounts such as social media. Knowing the importance of an email account, you can understand that the losses of falling victim to a hacked email is unmeasurable.
Although identifying the hacker behind it can be tricky, you can get to know their IP address. If you manage to find some clues about their identity, including name and online username, a reverse lookup on a people search site may allow you to dig deep. In addition to tracking down the hacker, you should learn how you can prevent future hacks by staying vigilant online and subscribing to an identity theft protection service to get alerts when your personal data has been compromised.

 View all of Sammi Liu's posts.
View all of Sammi Liu's posts.