Data Breach check: how to protect yourself after a data breach

Get Proactive Online Protection Today.
Try a no-risk 14-day free trial today.
Similar to thieves stealing at night, cybercriminals and hackers often break into the huge databases of big companies and organizations to steal confidential customer account information. Once the sensitive information is exposed to the public, it can have serious implications for countless people. In fact, sensitive information exposure can have serious repercussions for individuals, businesses, and governments.
If you’re uncertain whether your personal data was compromised or not in a data breach, you’re not alone! In this article, we’ll explain what a data breach is, how to run a data breach check to see if your personal information has been leaked, and how to prevent being a data breach victim. After reading it, you’ll learn everything you need to know about data breach.
What is a data breach?
A data breach, or a data leak, exposes sensitive, protected, or confidential information to an unauthorized person. It usually occurs when cybercriminals and hackers hack into databases and steal sensitive information.
It’s a security infringement that causes serious damage to both companies and consumers. The sensitive information, which is exposed to the public, can include account credentials, names, phone numbers, home addresses, and even Social Security Numbers and more.
How do data breaches happen?
Although many people think that a data breach is caused by an outside hacker, that’s not always true. Data breaches can sometimes be traced back to deliberate attacks. It could, however, be the result of simple oversight by individuals or flaws in a company’s infrastructure.
Here’s how a data breach can occur:
- An accidental insider. An example would be an employee using a co-worker’s computer and viewing files without having the proper authorization permissions. In this scenario, the access is unintentional, and no information is shared. However, the data is considered breached because it was accessed by an unauthorized person.
- A Malicious insider. This person accesses and/or shares sensitive information on purpose with the intent to cause harm to an individual or company. The malicious insider may be authorized to use the data, but the intent is to use it in nefarious way.
- Malicious outside criminals. These are hackers who steal sensitive information from a network or an individual using a variety of attack methods.
- Lost or stolen devices. An unlocked laptop or unencrypted external hard drive—anything that contains sensitive information—goes missing.
The damage a data breach can do
Account information exposed in data breaches can lead to identity theft, which is a major threat to data breach victims. In many cases, data breaches cannot just be patched with a few password changes. The adverse effects of a data breach can be a lasting issue for your privacy, finances, reputation, and more.
Your sensitive information—from your account credentials to your Social Security Number and banking information—are all at risk after a data breach. Once a criminal gets these details, they can commit all types of fraud under your name. In other words, identity theft can run your credit and land you in legal trouble, and it’s quite difficult to fight back.
While these are common cases, the damage caused by data breaches can go far beyond these. So, it’s essential that you run a data breach check and see if your data has already been exposed.
How to run a data breach check
It’s quite easy to run a data breach check, and all you need is a data breach checker. There are lots of data breach checkers out there, and if you don’t know which one to trust, here we recommend Aura’s free data breach checker.
Aura is an all-in-one intelligent digital security solution that protects you and your family from online threats, financial fraud and identity theft. Simple to understand and easy to use, Aura is one of the best digital security products out there, offering not only monitoring and account tracking, but also antivirus, password manager, and VPN services.
With Aura’s free data breach checker (aka dark web scanner), you just need to enter the email address you use most frequently, then Aura’s dark web scanner will check if information tied to your email has been exposed in data breaches or on the Dark Web. Here’s how to do it:
- Go to scan.aura.com.
- Enter your email address and click View Result.
- Wait a few seconds and Aura will tell you if it has found exposed data for your email address. You’ll need to scroll down to view the result.
If Aura didn’t find any exposed data for your email account, then congratulations!
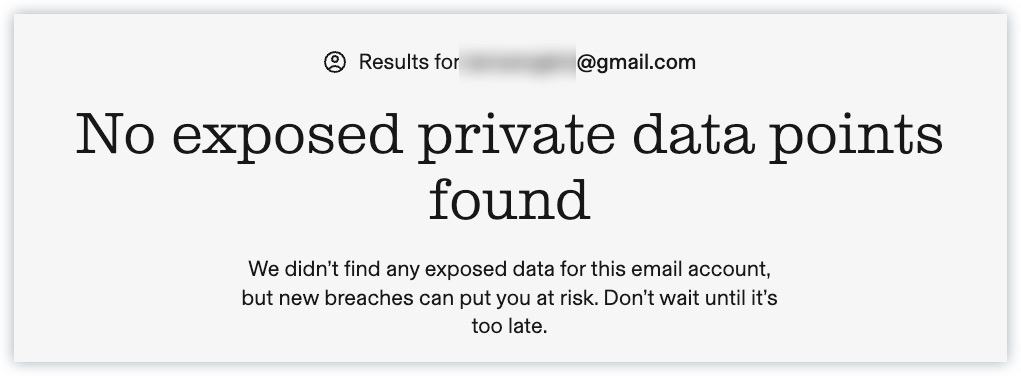
If it turns out that your private data is unfortunately leaked, don’t worry. products like Aura offers a comprehensive data leak detection and can help you navigate the situation.
How to prevent being a data breach victim
Data breaches happen from time to time. Even if there is no exposed data for your email account, new breaches can put you at risk. So, the best way to protect yourself is to avoid being a victim in the first place.
Here’re some best practice to avoid data breach:
For companies and organizations:
- High-grade encryption for sensitive data.
- Patching and updating software as soon as options are available.
- Upgrading hardware when the software is no longer supported by the developer.
- Enforcing strong passwords and multi-factor authentication.
- Enforcing BYOD security policies and making sure all devices are using a VPN service and antivirus protection.
- Training and educating employees on best security practices and methods to avoid socially engineered attacks.
For individuals:
- Use unique passwords for different accounts, and always use strong passwords.
- Always enable multi-factor authentication when available.
- Use a VPN when you’re using a public WiFi.
- Keep your important files in a safe place and encrypt them if necessary.
- Run antivirus software on your device.
- Never click on suspicious links.
- Consider using a digital security suite like Aura.
Bonus tip: use Aura to protect you and your family from digital threats
With over 20 years of experiences in identity theft protection, Aura provides all-in-one digital security solutions to protect your identity, finances, credits, and devices from threats.
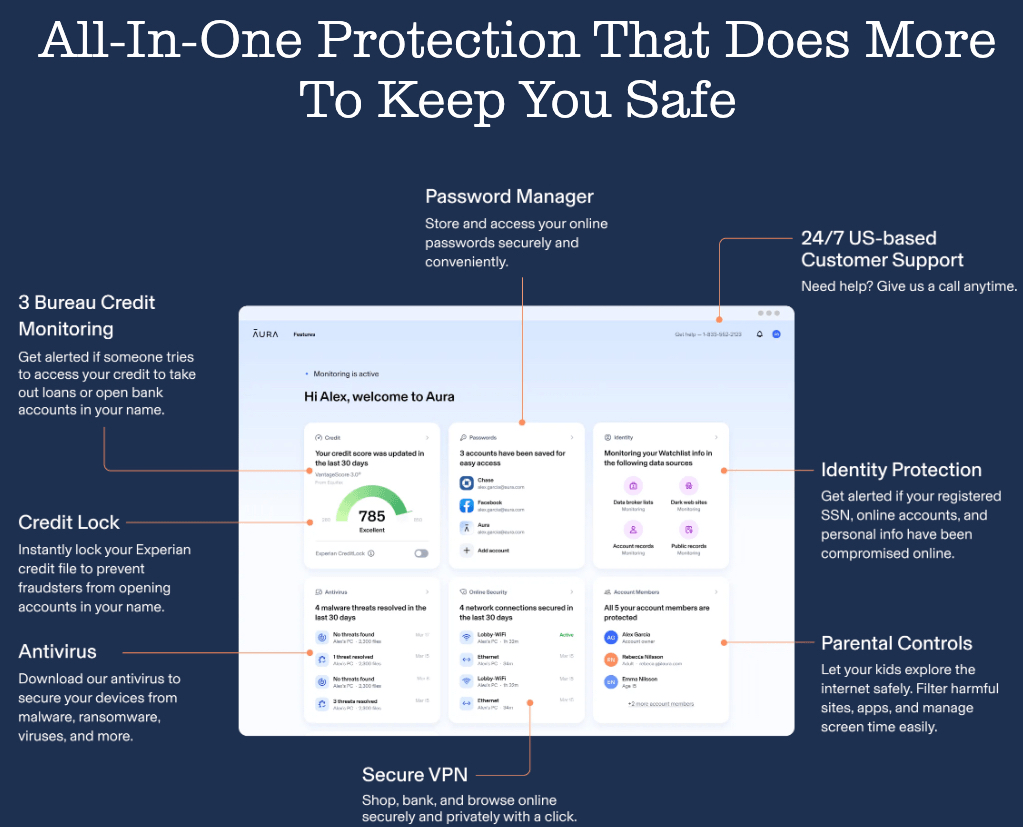
To keep you and your family safe, Aura offers the following features:
- Identity Protection
- Password manager
- Antivirus
- Secure VPN
- Parental controls
- Credit lock
- 3 bureau credit monitoring
- 24/7 US-based customer support

Get Proactive Online Protection Today.
Try a no-risk 14-day free trial today.
What to do if your data was compromised
If you learn that your data have been compromised, or notice suspicious activities on your accounts, follow the steps below to minimize losses:
To minimize losses after a data breach:
- Confirm the breach and identify what data was leaked
When a data breach happens, it is usually reported on many news sites, and you can confirm it on the official company site. Running a dark web scan is also a good way to check if your data was compromised.
- Lock down your accounts
Once you realize your account information has been exposed in a data breach, you need to change the password of the affected account. Note that you also need to update the passwords for any other accounts that use the same password.
You should choose unique passwords that are at least 12 characters long and include uppercase and lowercase letters, numbers and symbols.
If you don’t want to do it manually, Aura’s password manager is a good helper.
If possible, you need to set up two-factor authentication (2FA) for all sensitive accounts. - Secure your credit
If your Social Security Number has been leaked, criminals may apply for credit in your name. You need to secure your free credit reports from AnnualCreditReport.com and review it for any suspicious activity like incorrect balances, new accounts or credit checks that you don’t recognize.
You may also consider setting up a fraud alert or security freeze at the three major credit bureaus (Experian, TransUnion, and Equifax). - Notify authorities
Follow the Federal Trade Commission’s (FTC) specific recommendations for data breaches.
Report identity theft at IdentityTheft.gov and follow the instructions for further action if you are aware that someone has already used your data improperly.
Also report the theft the FBI’s Internet Crime Complaint Center at IC3.gov.
File an identity theft report with local law enforcement if you require additional documentation during the recovery process.
Image by rawpixel.com on Freepik




 View all of Justin Zeng's posts.
View all of Justin Zeng's posts.